VULNERABILITY SCANNING
Identify and eliminate vulnerabilities in your IT before they can be exploited by hackers. Our state-of-the-art vulnerability scanning service is designed to support your vulnerability management process with clear reporting that helps managers make informed decisions, while also providing technical staff with precise actionable information.
Services & Products
VULNERABILITY SCANNING SERVICE
We perform a series of checks of your systems using a wide variety of software tools including commercial scanning tools, as well as open source software that a potential attacker might use to identify vulnerabilities. Our scanning and reporting process is also highly scalable due to a novel approach to automation on our side, which allows us to offer our services at a very attractive price.
Vulnerability Scan
A thorough scan of the targetted systems to detect known vulnerabilities. The results are summarized in a regular status report that provides both management-level guidance and in-depth technical information about each finding. Each report also highlights changes relative to the previous report, and recommends solutions to resolve any remaining threats.
CERTIFICATE CHECK
This checks the expiry date of all SSL certificates associated with the targetted systems, and checks for cipher conformity. The report alerts administrators about certificates that are almost due to expire so they can be renewed in time to avoid any costly or embarrassing service disruptions.
PORT SCAN
A thorough scan to detect open TCP and UDP ports on the targetted systems. The report highlights changes relative to the previous status report and provides details of the services that are likely running on each of the detected ports.
CUSTOMIZATION
We can also offer customized reporting solutions to suit your business needs including long-term tracking of security vulnerabilities, which is especially suitable for auditing purposes.
IT SECURITY CONSULTING
As a company, we have been providing consulting services in the area of network and system security since our founding in 2005. We can help you design and implement a robust and scalable network structure from scratch, or harden the security of your existing network to keep your systems, and the personal data of your customers as secure as possible.
SECURITY POLICY
Define criticality levels for network segments or systems, set up clear rules for third parties and employees, and manage IT resources based on their criticality level and need-to-know.
NETWORK TOPOLOGY and SECURITY
Design and support secure network structures to protect critical infrastructure. We can also help you set up processes to monitor and react to threats based on network traffic.
VULNERABILITY MANAGEMENT
Set up an efficient and effective workflow for vulnerability management to keep your IT secure.
INTRUSION DETECTION
Set up an efficient and effective workflow for real-time intrusion detection and automated prevention.
ciproc Vulnerability Scanning Services
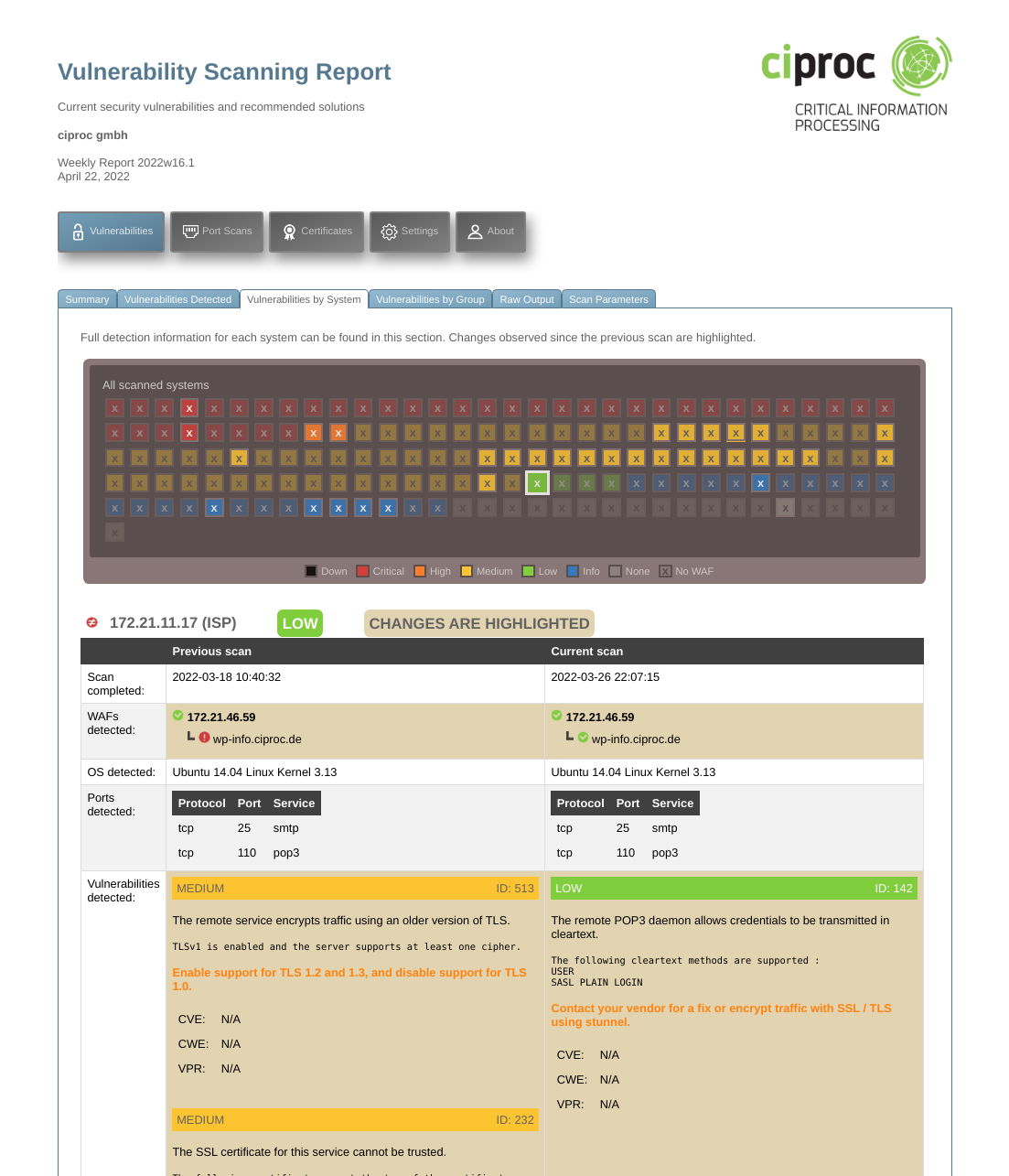
Vulnerability Scan
We perform a series of checks of your systems using a wide variety of software tools including commercial scanning tools, as well as open source software that a potential attacker might use to identify vulnerabilities. Our scanning and reporting process is also highly scalable due to a novel approach to automation on our side, which allows us to offer our services at a very attractive price.
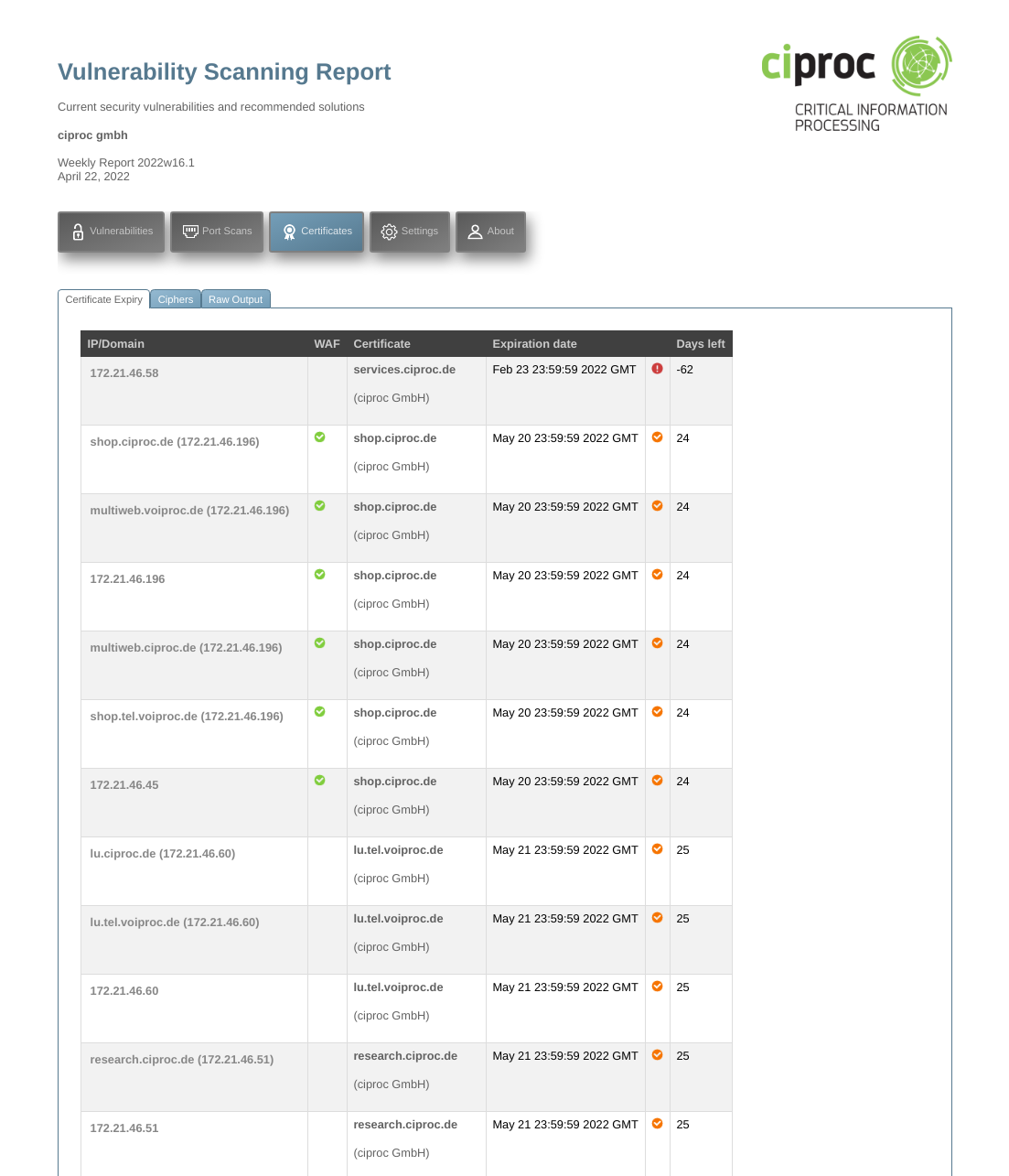
CERTIFICATE CHECK
This checks the expiry date of all SSL certificates associated with the targetted systems, and their associated encryption algorithms. The report alerts administrators about certificates that are almost due to expire so they can be renewed in time to avoid any costly or embarrassing service disruptions. It also provides warnings about insecure encryption schemes.
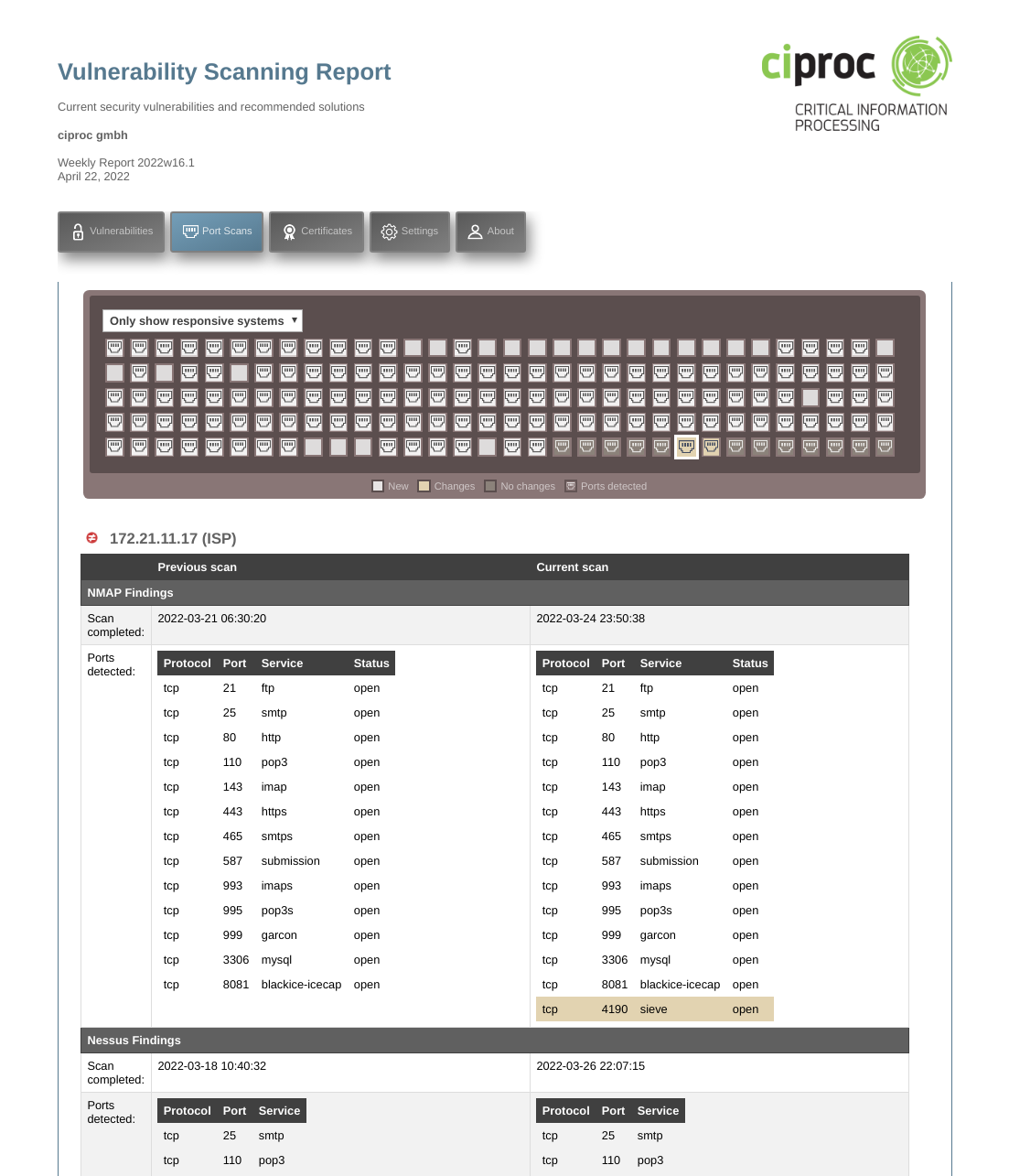
Port scan
A thorough scan to detect open TCP and UDP ports on the targetted systems. The report highlights changes relative to the previous status report and provides details of the services that are likely running on each of the detected ports (HTTP, SMTP, FTP, etc.). The one-line summary and color-coded system grid give you an overview of the changes at a glance.
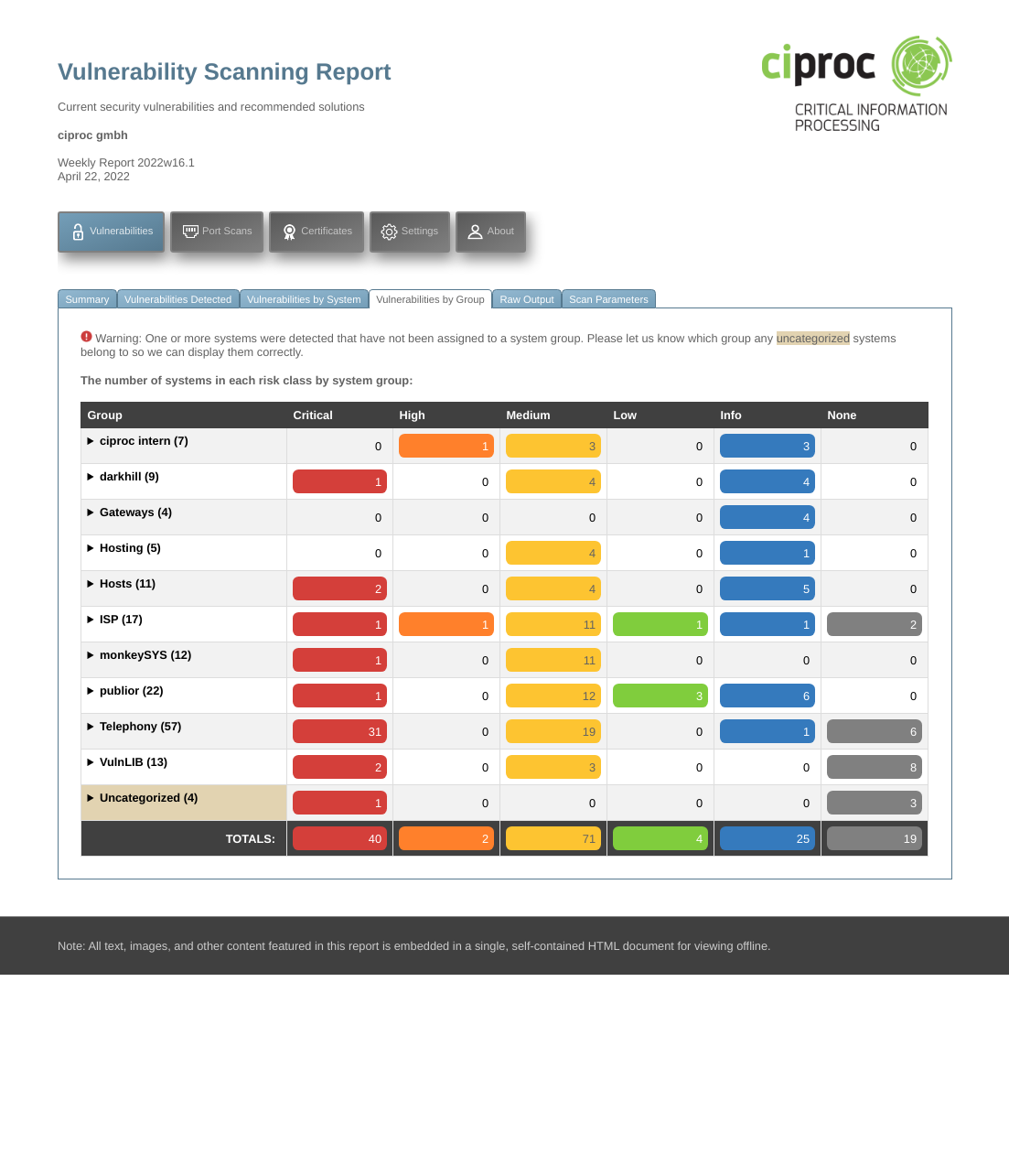
CUSTOMIZATION
We can also offer customized reporting solutions to suit the vulnerability management process of your business including long-term tracking of security vulnerabilities, which is especially suitable for auditing purposes.
ciproc Vulnerability Scanning Cycle
Scan
First, systems or networks are scanned and results are collected. Both, open-source and commercial tools are used.
PLAN
If necessary, further steps are coordinated with the customer and corresponding special scans or more comprehensive reports and analyses are planned.
Review
The collected results are reviewed by our analysts and, if necessary, further scans are initiated.
REPORTS & ALARMS
The results are then compiled in a fully customizable report. Critical findings are communicated directly to the customer without waiting for the report.